Haiku presents us with a challenge to battle another user (just a bot) in haiku writing. The backend actually uses NLTK to “grade” and make sure that both haiku adhere to the 5-7-5 construct for haiku. I wrote it a long time ago and don’t actually recall much of the inner workings of the grading mechanism, but that doesn’t really matter anyways.
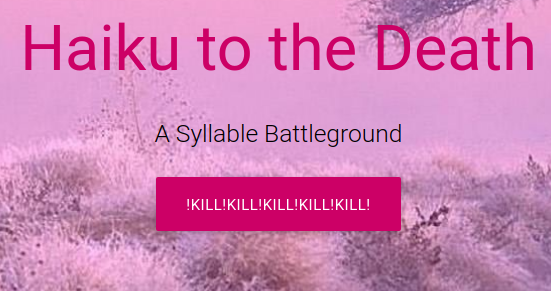
The site tells you that if you win 3 times you can enter a drawing for a chance to win a prize. First things first, we need to write up a killer haiku that will beat the bot more often than not. Nah, we can just take one of the auto-generated haikus from the bot and continuously enter it until we see that we can enter the drawing.
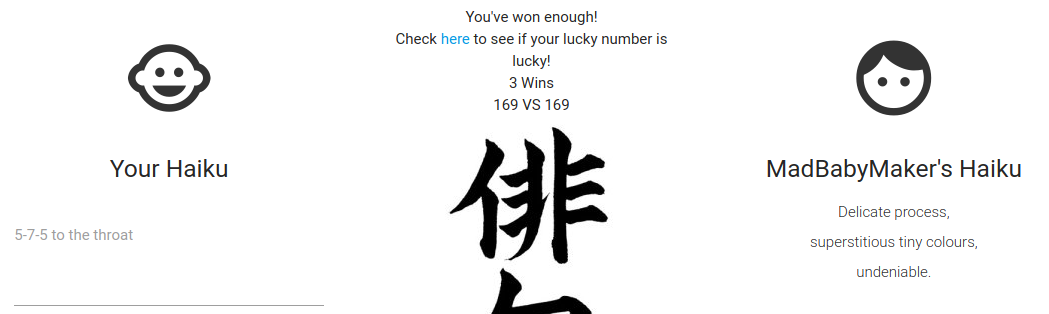
We also notice that we have an additional cookie, named winrar.
Looking at the content, appears to be base64 encoded, the leading eyJ…) really stand out that it will end up being a dictionary-like data structure most likely.
$ echo -n ‘eyJsdWNreV9udW1iZXIiOiAiMzYzNCJ9’ | base64 -d
{“lucky_number”: “3634”}
That looks super promising. Anyways, to continue with checking out all the functionality, let’s check the drawing page and see if we’ve won.

We did not win, but it looks like it used the same lucky_number from our winrar cookie. The site allows you to just keep trying the drawing so we can fiddle with the cookie and just refresh the drawing page.
$ echo -n ‘{“lucky_number”: “xxx”}’ | base64
eyJsdWNreV9udW1iZXIiOiAieHh4In0=
Let’s feed it some garbage first and see what happens.

That is kinda promising. Our number is now 0 and there is a message about the site breaking (not a true 500 error, must be catching it on the backend). That may be JSON or maybe we are lucky and they are just running eval on that cookie. Let’s send it some python and hope for the latter!
$ echo -n ‘{“lucky_number”: open(“flag.txt”).read()}’ | base64
eyJsdWNreV9udW1iZXIiOiBvcGVuKCJmbGFnLnR4dCIpLnJlYWQoKX0=
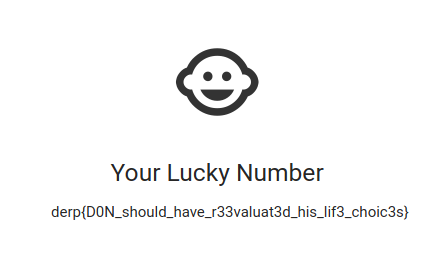
derp{D0N_should_have_r33valuat3d_his_lif3_choic3s}