While I’m still kinda halfway in CTF mode I thought I’d knock out one more this weekend. This was the only reversing challenge that was up on BioTerra. Although I did waste a lot of time on this one trying to figure out what input it wanted in order to print out the correct flag, it seems that any input was wholly unnecessary. Oh well, lessons learned. It did force me to finally get pin working in 64 bit mode though, so that’s always a plus. Anywho, on with the description
Only the chosen ones have the gift to read between the lines. We got this binary here. It does more than one may think.
As stated earlier, I spent more time than I should have tossing random things at it to see what I could get it to do. Once I felt that I had wasted a sufficient amount of time I ran it through strings to see if there was anything interesting in there. Lo and behold, there was!
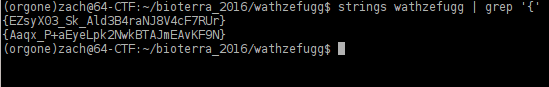
Two very Flagish looking strings, indeed.
Then it was time to run it through gdb and ni my way through it. I could see the two different ‘flag type’ strings being pushed into and out of the registers as well as them being chopped one char at a time from the start of the string, iterating back and forth like this until exhausted.
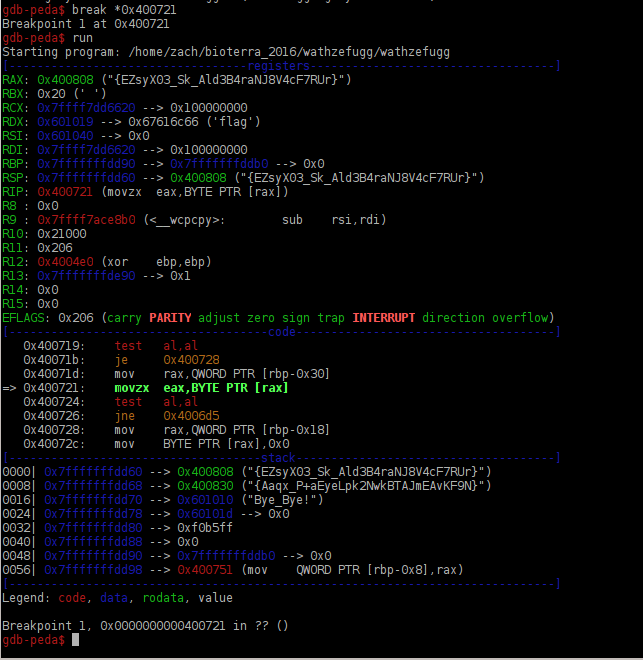
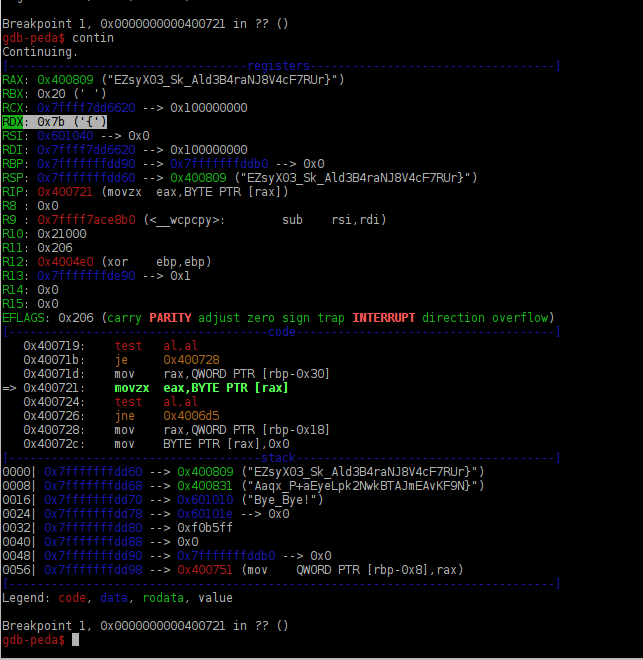
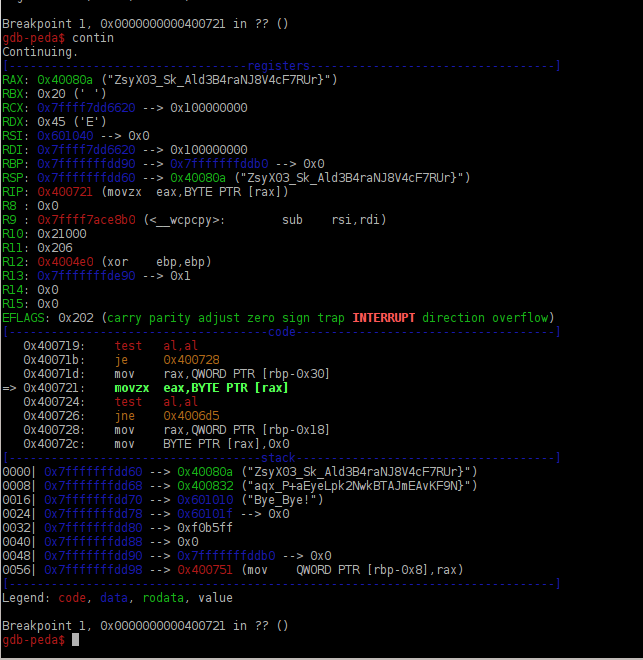
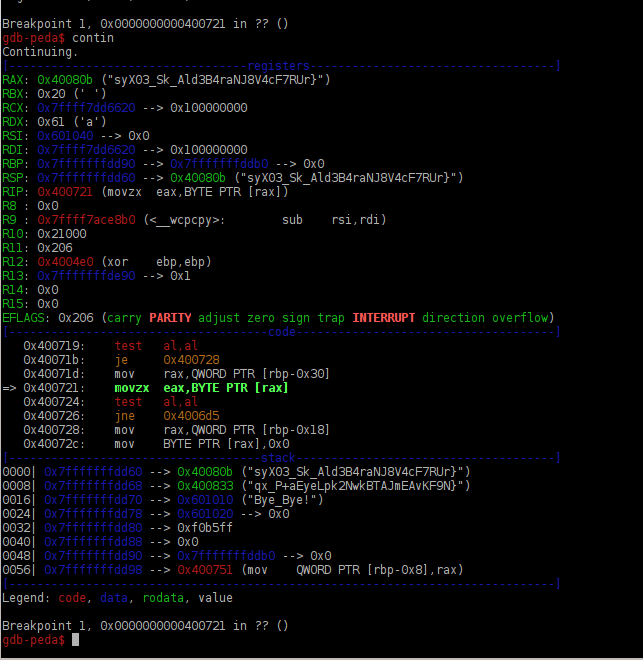
So it was going through and comparing one slice of each of those flag strings and selecting the one with the higher ordinal value, @MalwareJake can totally fill you in if you aren’t exactly, uh, ?up to speed? on ascii ranges).
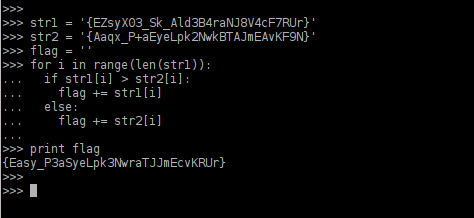
So I’m pretty lazy and decided not to try and jot those down as it went through (hey, they’re pretty long…) So I just tossed the strings into a python interpreter and did a little loop to select the higher char and build out the proper flag
>>> str1 = '{EZsyX03_Sk_Ald3B4raNJ8V4cF7RUr}'
>>> str2 = '{Aaqx_P+aEyeLpk2NwkBTAJmEAvKF9N}'
>>> flag = ''
>>> for i in range(len(str1)):
... if str1[i] > str2[i]:
... flag += str1[i]
... else:
... flag += str2[i]
...
>>> print(flag)
{Easy_P3aSyeLpk3NwraTJJmEcvKRUr}
>>>
And here’s a pretty picture if you’re more into imagery and all that.
{Easy_P3aSyeLpk3NwraTJJmEcvKRUr}